Pushme Pullyou transistor experiments with 2N3904, 2N5089, OC76 and AC125
Posted 2007-10-17 in Effects by Johann.
I built Tim Escobedo’s Pushme Pullyou which is a simple DIY octaver.
It’s been said that the Pushme Pullyou sounds better/has a more pronounced octave the more mismatched the transistors are (in terms of gain, I think).
Pushme Pullyou sound clip
- Pushme Pullyou transistor experiments (MP3, 1.8 MB)
- Pushme Pullyou transistor experiments (Ogg Vorbis, 1.3 MB)
In this audio sample, I’m trying various transistors. These include the 2N3904 and 2N5089 which are NPN BJTs and OC76 and AC125 with are PNP Germanium BJTs.
- 2N5089 with OC76. Good octave-up.
- 2N3904 with OC76. Dirty but no octave-up.
- 2N3904 with AC125. Dirty but no octave-up.
- 2N5089 with AC125. Good octave-up, maybe a little better?
Corporate web abuse: The worst offenders from Cyveillance to PicScout
Posted 2007-10-15 in Spam by Johann.
Not all abuse in the web is caused by individual spammers and scrapers. Some companies abuse other people’s web servers a lot more than the average comment spammer.
Blocking spambots and bad bots by user agent is less effective against corporate abusers who stealth crawl web sites. The best option is to block their networks by IP address.
In this blog entry, I’ll describe 7 web abusers, what they do and how you can prevent them from entering your website.
Cyveillance
Cyveillance does the dirty work for the RIAA and the MPAA.
[They scan and try] to gain unauthorized access to P2P networks, Web servers, IRC servers, FTP servers, and mail servers, accross the net looking for MP3s, and movie titles. They will even go as far as to attempt to break into your systems… After the scanning is done, the site is archived, and the information sold the the RIAA, and MPAA, so that they can turn around and sue your 12 year old child, or 80 year old grandmother, and get away with it.
Evidence
38.100.41.100 … "GET …JavaScript... HTTP/1.1" 403 1971 "news:1187732779.931620.254640@a39g2000hsc.googlegroups.com" "Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)" "-" 38.100.41.100 … "GET /help/sitemap.html HTTP/1.1" 403 1971 "…" "Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)" "-" 38.100.41.100 … "GET / HTTP/1.1" 403 1971 "…" "Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)" "-" 38.100.41.100 … "GET /help/copyright.html HTTP/1.1" 403 1971 "…" "Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)" "-" 38.100.41.100 … "GET /blablog/www/2006/06/08/ HTTP/1.1" 403 1971 "…" "Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)" "-" 38.100.41.100 … "GET /misc/handheld.css HTTP/1.1" 403 1971 "…" "Mozilla/4.0 (compatible; MSIE 6.1; Windows XP)" "-"
Netblocks
38.100.19.8/2938.100.21.0/2438.100.41.64/2638.105.71.0/2538.105.83.0/2738.112.21.140/3038.118.42.32/2965.213.208.128/2765.222.176.96/2765.222.185.72/29151.173.0.0/16
More netblocks might be listed on the Cyveillance Exposed website. I believe Cyveillance frequently obtains new netblocks and drops old ones. I have tried to find all but I cannot guarantee the above list is complete.
Websense, Inc.
Websense does stealth crawling and domain scanning with various user agents. I believe they are triggered when you ping Moreover.
Evidence
208.80.193.47 … "GET / HTTP/1.0" 403 345 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; Q312465)" "-" 208.80.193.43 … "GET / HTTP/1.1" 403 345 "-" "Mozilla/5.0 (compatible; Konqueror/3.1-rc1; i686 Linux; 20020921)" "-" 208.80.193.38 … "GET ….html?page=comments HTTP/1.1" 403 3735 "-" "Mozilla/5.0 (compatible; Konqueror/3.1-rc6; i686 Linux; 20021203)" "-"
Netblocks
66.194.6.0/24208.80.192.0/21204.15.64.0/21
VeriSign Infrastructure & Operations
I covered the stealth scaping and domain scanning going on in these netblocks before. Basically, a bunch of browser-looking user agents request robots.txt and then the root directory.
Evidence
208.17.184.48 … "GET /robots.txt HTTP/1.1" 403 1933 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.7.12) Gecko/20050922 Fedora/1.0.7-1.1.fc4 Firefox/1.0.7" "-" 208.17.184.48 … "GET / HTTP/1.1" 403 1933 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.7.12) Gecko/20050922 Fedora/1.0.7-1.1.fc4 Firefox/1.0.7" "-" 69.36.158.62 … "GET /robots.txt HTTP/1.1" 301 0 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.7.12; ips-agent) Gecko/20050922 Fedora/1.0.7-1.1.fc4 Firefox/1.0.7" "-" 69.36.158.62 … "GET / HTTP/1.1" 301 0 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.7.12; ips-agent) Gecko/20050922 Fedora/1.0.7-1.1.fc4 Firefox/1.0.7" "-" 69.36.158.63 … "GET /robots.txt HTTP/1.1" 403 345 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.7.12; ips-agent) Gecko/20050922 Fedora/1.0.7-1.1.fc4 Firefox/1.0.7" "-" 69.36.158.63 … "GET / HTTP/1.1" 403 345 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.7.12; ips-agent) Gecko/20050 922 Fedora/1.0.7-1.1.fc4 Firefox/1.0.7" "-"
Netblocks
69.36.144.0/2069.58.176.0/2072.13.32.0/19208.17.184.0/24
Blue Coat Systems, Inc.
Blue Coat builds web proxies with malware and content filtering built-in. Their proxy software pre-fetches content as quickly as possible which makes it look like an abusive scraper. Blue Coat also stealth crawls the web.
Evidence
217.169.46.98 … "GET /software/nativecall HTTP/1.1" 403 3735 "-" "Mozilla/4.0" "-" 217.169.46.98 … "GET /software/nativecall/url(%22/misc/handheld.css%22)%20handheld HTTP/1.1" 403 3735 "-" "Mozilla/4.0" "-" 217.169.46.98 … "GET /blog/music/effects/Kay-Fuzz-Tone.html HTTP/1.1" 403 3735 "-" "Mozilla/4.0" "-" 217.169.46.98 … "GET /blog/music/effects/url(%22/misc/handheld.css%22)%20handheld HTTP/1.1" 403 3735 "-" "Mozilla/4.0" "-"
Netblocks
8.21.4.254(?)65.46.48.192/3065.160.238.176/28204.246.128.0/20208.115.138.0/23216.16.247.0/28217.169.46.96/28
Secure Computing
Secure Computing scan the web looking for viruses and malware. Or so. The problem is they’re just guessing URLs which is not exactly showing a lot of cleverness.
Evidence
206.169.110.66 … "GET /main.htm HTTP/1.1" 403 1720 "-" "page_prefetcher" "-" 206.169.110.66 … "GET /main.php HTTP/1.1" 403 1720 "-" "page_prefetcher" "-" 206.169.110.66 … "GET /public.html HTTP/1.1" 403 1720 "-" "page_prefetcher" "-" (repeat ad nauseam)
Netblocks
206.169.110.0/24
MarkMonitor
MarkMonitor scans the web for phishing websites and counterfeit products. Unfortunately, I’m not selling anything nor do I want your credit card number so it’s safe from my perspective to block MarkMonitor.
Evidence
They cause a ton of requests to the same file which indicates a badly written bot. Or a desperate attempt at trying to find out if the page uses cloaking.
64.124.14.109 … "GET …already.html HTTP/1.1" 200 11723 "-" "Mozilla/5.0 (Windows; U; Windows NT 5.0; en-US; rv:0.9.4) Gecko/20011128 Netscape6/6.2.1" "-" 64.124.14.100 … "GET …already.html HTTP/1.1" 200 11723 "-" "Mozilla/5.0 (compatible; Konqueror/3.1; Linux; en)" "-" 64.124.14.100 … "GET …already.html HTTP/1.1" 200 11722 "-" "Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.6) Gecko/20040218 Galeon/1.3.12" "-" 64.124.14.101 … "GET …already.html HTTP/1.1" 200 11715 "-" "Mozilla/5.0 (Windows; U; Win 9x 4.90; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0" "-" 64.124.14.101 … "GET …already.html HTTP/1.1" 200 11576 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; DigExt)" "-"
Netblocks
64.124.14.0/25
PicScout
Little is known about PicScout, only that they stealth scan the web for unauthorized uses of images of Getty and those of other clients. Generally, whenever you have a company doing the dirty work for other seemingly legit companies, I recommend blocking all of them.
Netblocks
82.80.248.0/21. Bezeqint-Hosting. This is where the actual crawler is running from.62.0.8.0/24. PicScout. Employee office?206.28.72.0/21. Getty images.
Evidence
Their crawler changes user-agents mid-way. Its crawl rate borders on DOS attacks.
82.80.249.145 … [22/Sep/2007:04:52:23 +0200] "GET …content.html HTTP/1.1" 200 11020 "…" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; (R1 1.1); .NET CLR 1.1.4322)" "JSESSIONID=OMFGBPKMCFEN" 82.80.249.145 … [22/Sep/2007:04:52:23 +0200] "GET …content.html HTTP/1.1" 200 11012 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322)" "-" 82.80.249.145 … [22/Sep/2007:04:52:26 +0200] "GET …part-1.html HTTP/1.1" 200 9697 "…" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; (R1 1.1); .NET CLR 1.1.4322)" "JSESSIONID=OMFGBPKMCFEN" 82.80.249.145 … [22/Sep/2007:04:52:26 +0200] "GET …part-1.html HTTP/1.1" 200 9697 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322)" "-"
The verdict
Web abuse is big business. Fortunately, you can control who you want on your web site and who wont’t have access.
If your web hoster doesn’t let you control access to your web site (via .htaccess or lighttpd.conf for the lighttpd users), then choose another one. Protecting your web site from abuse should be in your interest and the one of your web hoster.
13 comments
Colorsound Overdriver sound clips: Insane boost and fuzz
Posted 2007-10-10 in Effects by Johann.
The Colorsound Overdriver produces the most insane amounts of boost and fuzz of any 9 V-powered stompbox.
The “overdrive” in “Overdriver” means overdriving your (preferably tube) amp with insane levels, not “overdrive” as in soft clipping. This is not a Tubescreamer!
The Colorsound Overdriver is one of the most fun pedals to play with. However, the master volume version is probably more versatile and easier to use than the master-less 70’s one I have.
Power Boost
It’s worth mentioning that the Colorsound Overdriver was also sold as the orange Power Boost. About which the macaris say:
the American market was ready for the sound but felt it looked a bit too . . . well . . .orange . So , it was rehoused in a grey hammerite case , called the Overdriver , Jeff beck made 'Blow by Blow' with it , and the rest , as they say , is a mystery . . I mean history !
Audio clips
In this sound clip, I’m playing my Ibanez 2027XVV into the Overdriver and then into my Boss VF-1 which adds amp simulation and a bit of reverb and delay. I gradually increase the volume and then tweak the bass and treble knobs.
Warning: The clip starts at a very low volume. Do not turn your volume up.
Note that you can still buy a new Colorsound Overdriver.
Dan Armstrong Green Ringer mods
Posted 2007-10-09 in Effects by Johann.
The Dan Armstrong Green Ringer is a simple but effective octave-up circuit that borders on ring modulation. By itself, it lacks a little character but in combination with an overdrive, the Green Ringer sounds great.
There’s been some of attempts to counter the problems of the Green Ringer circuit, add sustain, distortion and make the build easier.
Nulling mod
The Green Ringer nulling mod by JC Maillet adds a pot to balance the mixing of both half-wave rectified signals.
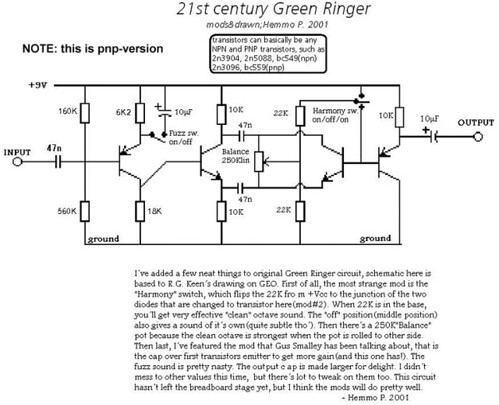
21st Century Green Ringer
The 21st century Green Ringer adds a gain boost and simplifies the signal mixing section.
Switchable filter mod
The Switchable Filter Mod also adds a gain boost and a low-pass filter for signal conditioning.
By the way, Grafton Electronics has started selling a stomp box version of the Green Ringer.
Pages
Page 12 · Page 13 · Page 14 · Page 15 · Page 16 · Page 17 · Page 18 · Next Page »
Subscribe
RSS 2.0, Atom or subscribe by Email.
Top Posts
- DynaCloud - a dynamic JavaScript tag/keyword cloud with jQuery
- 6 fast jQuery Tips: More basic Snippets
- xslt.js version 3.2 released
- xslt.js version 3.0 released XML XSLT now with jQuery plugin
- Forum Scanners - prevent forum abuse
- Automate JavaScript compression with YUI Compressor and /packer/